The Windows KMS keys are generic and basically tell Windows to go and look for your KMS server get get licensed.
Below is Microsofts list of keys to use.
http://technet.microsoft.com/en-us/library/jj612867.aspx
Friday 30 December 2011
Thursday 29 December 2011
CryptoCard - Outer Window Authentication
Not really deployment related but something I have been scratching my head over today. For a 2nd factor of authentication we run CryptoCard.
CryptoCard is wonderful, the way it works is that it knows what the next X number of possible codes that the shiny dongle of fun will generate (My guess is 3,600 of them).
In the “Policy Admin” screen there are some options for “Syncronization” the important ones are the top 2.
From the Crypto Hand-Book modified to make sense:
INNER EVENT BASED OTP WINDOW SIZE
This represents the number of passwords the server will “Look-ahead” from the last successful logon by the user.
Using an Example, if the user presses the button and does not use that number. The server will be expecting token number 1. But when the user authenticates they use token number 2. The server will look through token codes, 1 through to 10 (the default) and if a match is found they will be authenticated.
OUTER EVENT BASED OTP WINDOW SIZE
When the entered token code is not found in the Inner Event Based OTP Window the server will check the next set of codes up to the limit in the Outer Event Based setting (default 100). If a token code match is found the user will need to resync their token, in admin the web interface this can be seen with the “Result”: “Outer Window Authentication"
This leaves us with no real way to resync a token that is in this state. The options are to increase the OTP Window Sizes, or find some way to resync.
I have gone with both... 10 is a bit too few. Especially if the Crytpo box has a problem and users keep trying to login over a weekend.
The 2nd part was to have a way to actually do a resync when it is needed, since the proposed method on a crypto card requires the user to enter challenge codes on a token with 1 button... not ideal. The alternative isnt pretty but will do the job and get them logged in.
On the Crypto Server add the user as an Operator with the lowest privileges (Reporting). They give you the PIN and Token number which you use to login. The login page will prompt again for the login details telling you to enter the NEXT OTP (One Time Passcode).
Enter the username, PIN + Token number. You should see the reporting page. Log out, remove the Operator roles from the user and they can login as them selves from home.
Not ideal to add them to the server as an Operator, but they never attempt the logins (an admin does) and the roles should be removed straight away. Its got us out of a jam in a week that should have been quiet.
CryptoCard is wonderful, the way it works is that it knows what the next X number of possible codes that the shiny dongle of fun will generate (My guess is 3,600 of them).
In the “Policy Admin” screen there are some options for “Syncronization” the important ones are the top 2.
From the Crypto Hand-Book modified to make sense:
INNER EVENT BASED OTP WINDOW SIZE
This represents the number of passwords the server will “Look-ahead” from the last successful logon by the user.
Using an Example, if the user presses the button and does not use that number. The server will be expecting token number 1. But when the user authenticates they use token number 2. The server will look through token codes, 1 through to 10 (the default) and if a match is found they will be authenticated.
OUTER EVENT BASED OTP WINDOW SIZE
When the entered token code is not found in the Inner Event Based OTP Window the server will check the next set of codes up to the limit in the Outer Event Based setting (default 100). If a token code match is found the user will need to resync their token, in admin the web interface this can be seen with the “Result”: “Outer Window Authentication"
Junos Pulse doesnt handle the "Enter Next Token" bit properly and just comes up saying "BAD Passcode" and asks for a response. I tried everything I could think of, same code with and without pin, next code with and without pin and the same for the next 2 screens that come up. No luck.This leaves us with no real way to resync a token that is in this state. The options are to increase the OTP Window Sizes, or find some way to resync.
I have gone with both... 10 is a bit too few. Especially if the Crytpo box has a problem and users keep trying to login over a weekend.
The 2nd part was to have a way to actually do a resync when it is needed, since the proposed method on a crypto card requires the user to enter challenge codes on a token with 1 button... not ideal. The alternative isnt pretty but will do the job and get them logged in.
On the Crypto Server add the user as an Operator with the lowest privileges (Reporting). They give you the PIN and Token number which you use to login. The login page will prompt again for the login details telling you to enter the NEXT OTP (One Time Passcode).
Enter the username, PIN + Token number. You should see the reporting page. Log out, remove the Operator roles from the user and they can login as them selves from home.
Not ideal to add them to the server as an Operator, but they never attempt the logins (an admin does) and the roles should be removed straight away. Its got us out of a jam in a week that should have been quiet.
Labels:
CryptoCard,
Junos Pulse,
Outer Window Authentication,
resync
Friday 23 December 2011
SCCM OS Targeting by Collection
In cases like updates and such you may want to target machines based on what OS they are running.
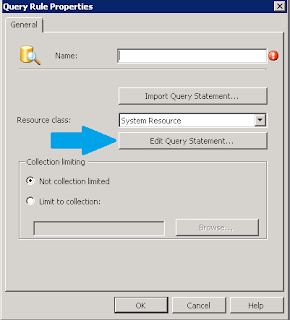
Create a new collection, and select a Query based rule
Give the rule a name, limit it to a collection if you wish. Click "Edit Query Statement..."
On the Query Statement Properties, click "Show Query Language". This will allow you to enter a statement rather than selecting fields manually.
Paste in the the query below, and change the <OSVERSION> with the version number below that.
Windows XP: Workstation 5.1
Windows 7: Workstation 6.1
Windows Server 2003: Server 5.2
Windows Server 2008: Server 6.0
Windows Server 2008 R2: Server 6.1
Save the query and the collection. Update and the collection will now contain all machines that have reported to be running that OS Version.
Create a new collection, and select a Query based rule
Give the rule a name, limit it to a collection if you wish. Click "Edit Query Statement..."
On the Query Statement Properties, click "Show Query Language". This will allow you to enter a statement rather than selecting fields manually.
Paste in the the query below, and change the <OSVERSION> with the version number below that.
select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System where SMS_R_System.OperatingSystemNameandVersion like "%<OSVERSION>%"
Windows XP: Workstation 5.1
Windows 7: Workstation 6.1
Windows Server 2003: Server 5.2
Windows Server 2008: Server 6.0
Windows Server 2008 R2: Server 6.1
Save the query and the collection. Update and the collection will now contain all machines that have reported to be running that OS Version.
Thursday 22 December 2011
SCCM Client Not Updating the server
PART 2, the more reliable solution
Post deployment clients are not talking to the SCCM server and updating it with their information.
The blog post here has some great information on how to solve the issue. What it doesnt cover is how to get the PC's you have rolled out already.
What J.C. Hornbeck does mention is where to correct it, the registry key:
HKLM\SOFTWARE\Microsoft\CCM\CcmExec\ProvisioningMode="true"
I have created a Group Policy Preference to change the "true" to a "false". Follow this up with the script from Microsoft here. If you are deploying this out there, comment all the "Echo" commands out so it gives no prompts and is 100% silent.
This is NOT a fix for the root issue, but gets the clients already deployed to comunicate back to the mothership
Remove Domain Group Policy from PC in a Workgroup
Scenario:
You build a PC using you favourite deployment method which adds it to a domain. The PC gets Group Policy but is then removed from the domain.
The computer policies are NOT removed... By design or a design flaw who knows.
Solution:
To remove the policies launch "regedit" and browse to:
"HKLM\Software\Microsoft\Windows\CurrentVersion\Group Policy"
Remove any keys starting with "S-".
Open the key "GroupMembership" and delete the entries starting with "S-" that you removed above.
You build a PC using you favourite deployment method which adds it to a domain. The PC gets Group Policy but is then removed from the domain.
The computer policies are NOT removed... By design or a design flaw who knows.
Solution:
To remove the policies launch "regedit" and browse to:
"HKLM\Software\Microsoft\Windows\CurrentVersion\Group Policy"
Remove any keys starting with "S-".
Open the key "GroupMembership" and delete the entries starting with "S-" that you removed above.
Reboot and you are now policy free.
Canonical Names for Windows 7 Control Panel
Obviously you don't want all users to be able to access every item inside of the Control Panel.
So in Group Policy you can set which items are visible/hidden. To do this in GP go to: "User Configuration" > "Policies" > "Administrative Templates" > "Control Panel"
Edit the policy with the Canonical names of the C Panel items.
http://msdn.microsoft.com/en-us/library/windows/desktop/ee330741(v=vs.85).aspx
The format from what I have seen is:
Default windows items have "Microsoft." at the start and no spaces in the name. For example "Microsoft.WindowsFirewall"
For everything else it is it's name as seen in the C Panel. For example "Configuration Manager" or "Mail"
So in Group Policy you can set which items are visible/hidden. To do this in GP go to: "User Configuration" > "Policies" > "Administrative Templates" > "Control Panel"
Edit the policy with the Canonical names of the C Panel items.
http://msdn.microsoft.com/en-us/library/windows/desktop/ee330741(v=vs.85).aspx
The format from what I have seen is:
Default windows items have "Microsoft." at the start and no spaces in the name. For example "Microsoft.WindowsFirewall"
For everything else it is it's name as seen in the C Panel. For example "Configuration Manager" or "Mail"
Friday 16 December 2011
Stopping Windows 7 UAC for an application
The Windows 7 UAC can be a problem with some older applications when they were made with little thought to how crazy MS could get.
Any exe that has "Setup" or "Install" anywhere in its properties will have UAC ask for elevation. To get around this the "Microsoft Application Compatibility Toolkit" was created.
Download, install and run this (Compatibility Administrator). Once launched, create a new database under "Custom Databases". Right click the DB > "Create New" and select "Application Fix"
Give the whole thing a name, and browse to the application exe that is causing an issue.
Select the Compatibillity Mode for some version of XP (XP SP2/3) and select "RunAsInvoker" under "Additional Compatability modes". This tells Windows 7 that this app should run as the user who launches it... as in, it doesnt need to be an admin.
From the Compatibility Fixes select, "AddWritePermissionsToDeviceFiles" and click Next
Below is the reason my app wouldnt work, "spv-setup"... on the running application file.
Your application database thing should look like this
Once all that is done, copy it somewhere and run the command as an admin. I deployed this via SCCM which manages all that for me. But running it without a full path didnt actually work. So I copied it locally in my install script.
Any exe that has "Setup" or "Install" anywhere in its properties will have UAC ask for elevation. To get around this the "Microsoft Application Compatibility Toolkit" was created.
Download, install and run this (Compatibility Administrator). Once launched, create a new database under "Custom Databases". Right click the DB > "Create New" and select "Application Fix"
Give the whole thing a name, and browse to the application exe that is causing an issue.
Select the Compatibillity Mode for some version of XP (XP SP2/3) and select "RunAsInvoker" under "Additional Compatability modes". This tells Windows 7 that this app should run as the user who launches it... as in, it doesnt need to be an admin.
From the Compatibility Fixes select, "AddWritePermissionsToDeviceFiles" and click Next
Below is the reason my app wouldnt work, "spv-setup"... on the running application file.
Your application database thing should look like this
Once all that is done, copy it somewhere and run the command as an admin. I deployed this via SCCM which manages all that for me. But running it without a full path didnt actually work. So I copied it locally in my install script.
copy "spv.sdb" "c:\spv.sdb"
sdbinst c:\spv.sdb
Tuesday 13 December 2011
Restoring a GPO from a file backup
After having GPMC crash on me today I was left with a GPO that I couldnt edit because it was "invalid". "Failed to open the group policy object the data is invalid"
Now I havn't made in backups inside of Group Policy and as such couldn't do a quick restore. What we do have is NetApp backing up the OS drive every hour... should be all I need. Well no, turns out the way to restore when you have the files is an Authorative Restore... shutting down the DC and going through a long winded process.
After some thought into it I came up with a work around. The GPMC works, so I backed up the problem GPO to disk. Inside of this backup is a copy of the files from the OS drive.
Replaced the issue registry.pol with one from the backup and restored it back into Group Policy. This did the trick, its an hour or so old but thats not too bad I hadnt made any changes since. Better than recreating the whole thing from scratch.
To locate the files in your backup restore, you need to get the UID of the GPO. Select the GPO in the GPMC and click the "Details" tab. The UID is highlighted below.
Next browse to:
"X:\Windows\SYSVOL\sysvol\<domain>\Policies\<UID>"
Where X is the drive the restore files are on. Replace
From here select either "Machine" or "User" for which ever part of the GP got corrupted... or both, or even just use this whole folder. Use these files to replace the corrupted ones in your GPMC backup and do a restore.
To do a backup or restore, right click the policy and follow what it says.
Hope this helps...
Now I havn't made in backups inside of Group Policy and as such couldn't do a quick restore. What we do have is NetApp backing up the OS drive every hour... should be all I need. Well no, turns out the way to restore when you have the files is an Authorative Restore... shutting down the DC and going through a long winded process.
After some thought into it I came up with a work around. The GPMC works, so I backed up the problem GPO to disk. Inside of this backup is a copy of the files from the OS drive.
Replaced the issue registry.pol with one from the backup and restored it back into Group Policy. This did the trick, its an hour or so old but thats not too bad I hadnt made any changes since. Better than recreating the whole thing from scratch.
To locate the files in your backup restore, you need to get the UID of the GPO. Select the GPO in the GPMC and click the "Details" tab. The UID is highlighted below.
Next browse to:
"X:\Windows\SYSVOL\sysvol\<domain>\Policies\<UID>"
Where X is the drive the restore files are on. Replace
From here select either "Machine" or "User" for which ever part of the GP got corrupted... or both, or even just use this whole folder. Use these files to replace the corrupted ones in your GPMC backup and do a restore.
To do a backup or restore, right click the policy and follow what it says.
Hope this helps...
Monday 12 December 2011
DEP and BitLocker
Enabling DEP (Data Execution Protection), or to change it its configuration is done in one of 2 ways.
Through Properties on Computer
Or using the command line "bcdedit /set nx "
Through Properties on Computer
Or using the command line "bcdedit /set nx "
Either method will work and do what you want it to (In my case it was OptOut which allows you to specify applications to be exempt from DEP).
The issue comes in when you are running OS disk encryption with BitLocker. Changing DEP settings changes boot.ini and as such will lock the user out of BitLocker requiring them to enter the recovery key until the PIN is changed. Even this may not stop them getting the prompt.
Obviously this isn’t ideal for a mass deployment, where having to manually change the BitLocker PIN for every user means you may as well manually set DEP.
The solution, start and stop BitLocker.
manage-bde -protectors -disable cThe above added to a batch script, or SCCM will pause BitLocker (and not prompt for a PIN), changes the setting for DEP in boot.ini and then restarts BitLocker.
bcdedit /set nx OptOut
manage-bde -protectors -enable c
When you stop BitLocker is irrelevant, as long as it is restarted AFTER you have made the changes to boot.ini. The same stop and start will be needed for some changes to the BIOS or hardware.
Subscribe to:
Posts (Atom)